Almost every business today relies on web or cloud applications for critical functions like connecting with customers & suppliers, performing financial transactions, or exchanging confidential information. There is a whole industry built around cloud software companies that provide multi-tenant applications services for specific for specific industry or business functions like CRM, Subscription Billing, Payment Services, Health Benefits, HR Management, etc. The practical real-world applications for web and cloud apps are endless. These apps, however, are an easy target for malicious attackers who attempt to get past the application security controls by crafting sophisticated application-layer attacks to obtain confidential data or perform illegal transactions. Our application security team brings the focus in finding these security holes before an attacker does.
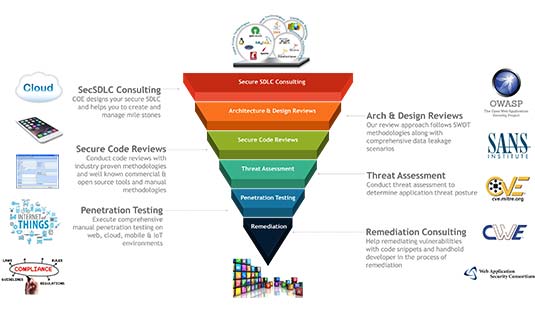
Our security penetration tests and application security scanning check for weaknesses against threats listed under OWASP Top 10, WASC Threat Classification and CWE/SNAS Top 25 combined with our own classified list built from many of application security testing experience. Source code review takes a hybrid approach using leading-edge automated tools, our scripts and source code review experts skilled in application development and security.
Because we are truly focused on being your trusted guide as you meet your application security and network risk management challenges. The services include an end to end application security and remediation guidance – covering penetration testing, code review, threat analysis, threat profiling, risk rating, business logic is driven security tests and comprehensive reporting.
Our customer information-centric approach to threats and vulnerabilities embeds security, risk and provides resilience in every customer engagement – what you are seeing here today gives you insight into our security threat management credentials, but quite frankly, threat management is a component of everything we do – whether it is a new account opening process for a bank or a migration to virtualization for the IT dept. It is part of our working ethos.
Want To Know More?
Get a Call Back From Our Cyber Expert
FAQs
What is enterprise security management?
Enterprise security management is a holistic approach to integrating guidelines, policies and proactive measures for various threats.
What is security solution?
The aim of the security solution is to protect the information and software that are important for the company and their loss or fall into the wrong hands could mean financial damage.
What is enterprise level security?
Enterprise application security refers to the protection of enterprise applications from external attacks, privilege abuse and data theft. By implementing security across all applications, enterprises can achieve greater data security and protect applications from vulnerabilities.
