The fifth-generation mobile networks (5G) will soon supersede 4G in most countries of the world. The next generation wireless network technology is being developed based on recent advances in wireless and networking technologies such as software-defined networking and virtualization. Compared to 4G technologies, 5G is characterized by still higher bit rates with more than 10 gigabits per second as well as by more capacity and very low latency, which is a major asset for the billions of connected objects in the context of Internet of Things (IoT).
In the IoT era, 5G will enable a fully mobile and connected society, via creating various new network services such as mobile fog computing, car-to-car communications, smart grid, smart parking, named data networking, blockchain based services, unmanned aerial vehicle (UAV), etc.
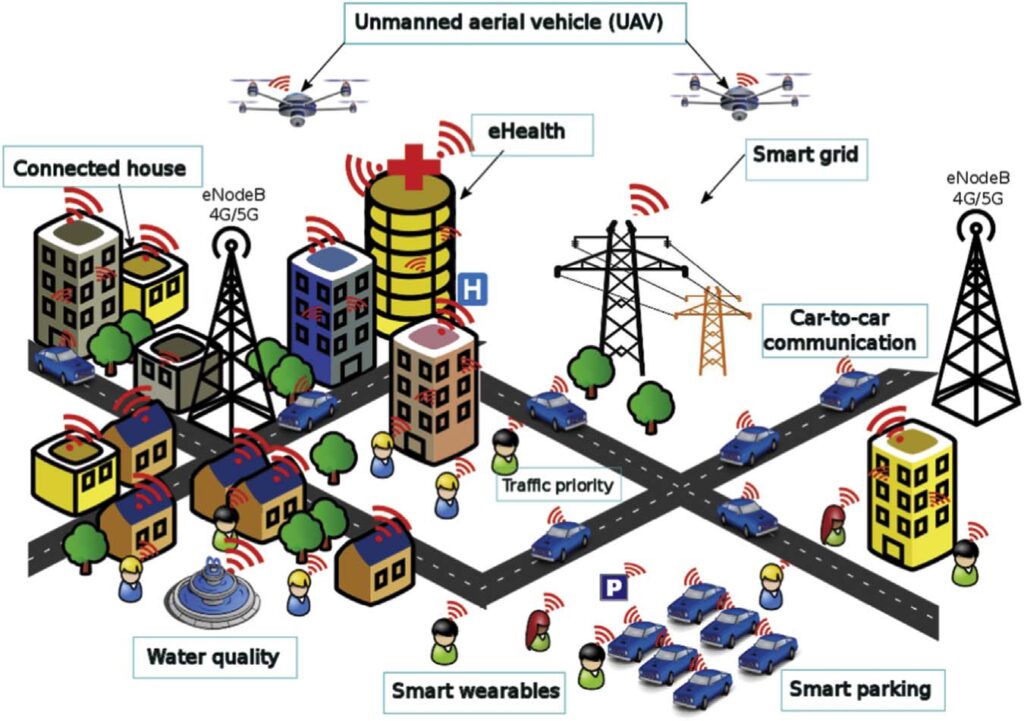
Our Team at Lancesoft leverage the 5G standardized security features which are defined in 3GPP standards to provide enhanced cybersecurity capabilities built into the network equipment and end-user devices. In addition, the project aims to identify security characteristics of the underlying technologies and components of the supporting infrastructure required to effectively operate a 5G network.
We will focus on operational real-world 5G solutions such as commercial 5G deployments and equipment used by carriers and private 5G implementations. The solution may utilize proprietary vendor products as well as commercially viable open source solutions. Security capabilities and administration of mobile devices are key components of adopting 5G.
Our cyber security experts focuses on the security implications of device connections to cellular networks. It leverages current and future NIST and industry guidelines and projects, such as the NCCoE’s Mobile Device Security project, for guidance for securing and administering mobile devices.
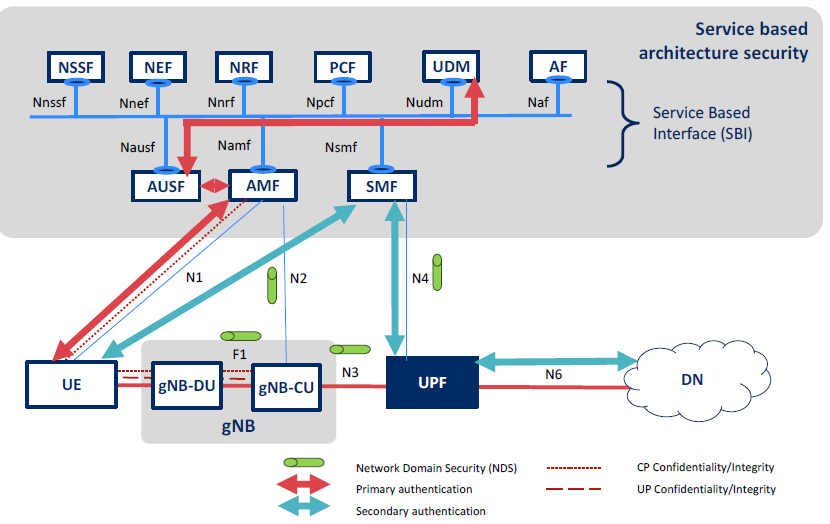
IMG: 5G Security Overview
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
Want To Know More?
Get a Call Back From Our Cyber Expert
FAQs
Why is 5G a security risk?
5G poses an elevated security threat partly because there are more vectors through which adversaries can attack. The technology is set to enable a huge number of connected devices, collectively known as the internet of things (IoT).
What is 5g security?
5G marks the beginning of a new era of network security with the introduction of IMSI encryption. All traffic data which is sent over 5G radio network is encrypted, integrity protected and subject to mutual authentication e.g. device to network.
How secure is 5G?
5G Is More Secure Than 4G and 3G—Except When It’s Not. The next-generation wireless networks make it harder to track and spoof users, but security holes remain because devices still connect to older networks.
